Aims and Goals of the Conference
In recent years, Multimedia Communications, Services and Security have been contributing extensively to our life experience and are expected to be among the most important applications in the future. The objective of the Multimedia Communications, Services & Security (MCSS’13) conference is to present research and developing activities contributing to aspects of multimedia communications, systems and security. We are inviting both theoretical and experimental papers as well as work-in-progress research. The main topics of interest are as follows:- Audio-visual systems including novel multimedia architectures and SOMA
- Multimedia and data fusion in personal, sensor, p2p and ad-hoc networks
- Acquisition of multimedia content and QoE management in content distribution networks
- Seamless mobility of multimedia services including mobile and wireless access networks
- Watermarking technology and applications
- Network measurement, monitoring and performance evaluation of multimedia services
- Reliability, availability, serviceability of multimedia services
- Searching methods, search engines and applications
- Multimedia surveillance and compound security, object tracking and threat detection
- Semantic description of multimedia data and metadata information systems
- Intelligent monitoring of objects and areas, recognition with automatic categorization
- Modern computing methods for multimedia systems and authentication of multimedia content
- Interactive multimedia applications
- Ethical issues and law aspects in video surveillance, Internet monitoring, security research
- Intelligent urban environment observation systems including safety monitoring and evacuation
- Cybercrime – threats and counteracting
- Cryptography and data protection, including quantum cryptography
- Evaluation of security features in end-user applications
- Parallel processing of audio & video, video processing through cloud computing, video transcoding
- Intelligent searching of multimedia content
- Biometric applications
- Privacy protection
Special sessions
A special session on intelligent monitoring, object tracking and threat detection will be organized along with the main conference. The MCSS conference will host not only technical program sessions, but there will also be an exhibition, where research groups can present their innovative achievements and prototypes in small booths or stands. We kindly ask for proposals of exhibition stands to present research outcomes. A parallel poster and demonstration session entitled “Demonstrations on MCSS” will be organized along with the main conference. This event encourages researchers to present and discuss the “work-in-progress” or “experience-in-practice” of their current studies/implementations and research prototypes which conform to the topics of MCSS’13.Keynote
The keynote speech will be given by professor K. R. Rao, University of Texas at Arlington. He is credited with the co-invention of discrete cosine transform (DCT), along with N. Ahmed and T. Natarajan due to their benchmark publication, N. Ahmed, T. Natarajan, and K. R. Rao, "Discrete Cosine Transform", IEEE Trans. Computers, 90-93, Jan 1974. Title: Current Video Coding Standards: H.264/AVC, Dirac, AVS China, HEVC and VC-1
Abstract: Video coding standards: H.264/AVC, HEVC, DIRAC, AVS China and VC-1are presented. These are the latest standards (HEVC is being finalized) and are adopted by ITU-T/ISO-IEC, BBC, China standards organization and SMPTE respectively. Besides presenting these standards, research potential and as well projects (both at UG and grad levels) are emphasized. These are available by accessing the database for research and projects. Web/ftp sites for accessing standards documents, software, test sequences, conformance bit streams, industry activities etc are provided.
Title: Current Video Coding Standards: H.264/AVC, Dirac, AVS China, HEVC and VC-1
Abstract: Video coding standards: H.264/AVC, HEVC, DIRAC, AVS China and VC-1are presented. These are the latest standards (HEVC is being finalized) and are adopted by ITU-T/ISO-IEC, BBC, China standards organization and SMPTE respectively. Besides presenting these standards, research potential and as well projects (both at UG and grad levels) are emphasized. These are available by accessing the database for research and projects. Web/ftp sites for accessing standards documents, software, test sequences, conformance bit streams, industry activities etc are provided.
Invited Speakers
 Piotr Konieczny will give a speech about the protection of our privacy online.
Title: We can protect our privacy online. NOT.
Biography: For the last 8 years Piotr has been working with both Polish and international
companies helping them increase the security of their networks and web
applications. A graduate of Glasgow Caledonian University. He began
his career in IT in the British division of Philips Electronics. Few years later he founded
Niebezpiecznik.pl, a consulting company focused on IT security. Within
Niebezpiecznik.pl Piotr manages the team responsible for penetration
testing and security audits of IT systems. In addition, he runs a series of popular security
trainings for programmers and system administrators.
Piotr Konieczny will give a speech about the protection of our privacy online.
Title: We can protect our privacy online. NOT.
Biography: For the last 8 years Piotr has been working with both Polish and international
companies helping them increase the security of their networks and web
applications. A graduate of Glasgow Caledonian University. He began
his career in IT in the British division of Philips Electronics. Few years later he founded
Niebezpiecznik.pl, a consulting company focused on IT security. Within
Niebezpiecznik.pl Piotr manages the team responsible for penetration
testing and security audits of IT systems. In addition, he runs a series of popular security
trainings for programmers and system administrators.
 Piotr Drobek will give a speech about privacy protection issues in scientific research.
Title: Dilemmas of privacy protection in researches on public security. Data Protection Authority’s point of view
Biography:
Piotr Drobek graduated from the University of Warsaw, Faculty of Law and Administration in 2000. In the same year he started working for the Bureau of the Inspector General for Personal Data Protection in Poland. Where currently he is a deputy director of the Social Education and International Co-operation Department. He is the Polish representative in the Joint Supervisory Body Europol and Joint Supervisory Authority Customs (since October 2012 as a vice chair) and other supervisory and consultative bodies responsible for personal data protection in the EU. He has been an expert of Council of Europe and European Commission in several projects, conferences and seminars. Mr Drobek runs trainings and lectures on data protection in various institutions. At present he is also a lecturer at the Cardinal Stefan Wyszyński University in Warsaw.
Piotr Drobek will give a speech about privacy protection issues in scientific research.
Title: Dilemmas of privacy protection in researches on public security. Data Protection Authority’s point of view
Biography:
Piotr Drobek graduated from the University of Warsaw, Faculty of Law and Administration in 2000. In the same year he started working for the Bureau of the Inspector General for Personal Data Protection in Poland. Where currently he is a deputy director of the Social Education and International Co-operation Department. He is the Polish representative in the Joint Supervisory Body Europol and Joint Supervisory Authority Customs (since October 2012 as a vice chair) and other supervisory and consultative bodies responsible for personal data protection in the EU. He has been an expert of Council of Europe and European Commission in several projects, conferences and seminars. Mr Drobek runs trainings and lectures on data protection in various institutions. At present he is also a lecturer at the Cardinal Stefan Wyszyński University in Warsaw.
Call for Papers
Download the Call for Papers: Adobe PDF, 223 kB
Adobe PDF, 223 kB
Paper Submission
Copyright forms: the copyright forms are available on the Springer's CCIS page.
Update: The conference proceedings will be published in Springer's CCIS. Please refer to the details below for more information. At the same time the maximum paper length has been extended to 15 pages.
Please adhere to the standard manuscript template of Springer-Verlag LNCS (http://www.springer.com/computer/lncs?SGWID=0-164-6-793341-0). The recommended paper length is 10-12 pages. The maximum paper length is 15 pages, including tables and figures. The cover page must contain an abstract of about 150 words, 3-5 keywords, name and affiliation of author(s) as well as the corresponding author's e-mail and postal address.
Consistent with standard practice, each submitted paper will receive rigorous peer reviewing. Papers
will be selected based on their originality, timeliness, significance, relevance and clarity of presentation.
The selection will be based on full papers. Submission implies the willingness of at least one of the
authors to register and present the paper, if accepted. All papers accepted to the conference are
expected to be presented.
Publication of the Conference Proceedings
The proceedings of the MCSS 2013 will be published in the Communications in Computer and Information Science (CCIS) series from Springer. You can find more information about the series at http://www.springer.com/series/7899. The proceedings from previous editions of the conference are available at:- MCSS 2011, http://www.springer.com/978-3-642-21511-7.
- MCSS 2012, http://www.springerlink.com/content/978-3-642-30720-1.
Submission System
Submissions are handled by EDAS: http://edas.info/N13623.Special Issue of Multimedia Tools and Applications
A special issue of the journal Multimedia Tools and Applications on the topic of Multimedia Communications, Systems, and Security will be open for submission after the conference. Selected highest quality papers from the conference, will be invited to prepare extended versions of the manuscripts for consideration to the journal. The extended papers will receive rigorous peer review, performed by experts in the field.Important Dates
Submission: 10 Jan 2013Submission: 1 Feb 2013
Notification: 20 Feb 2013
Notification: 1 Mar 2013
Camera ready: 10 Mar 2013
Conference: 6 - 7 Jun 2013
Conference Program
| Thursday, 2013-06-06 | |||
| 8:00-9:30 | Registration | ||
| 9:30-9:50 | Opening | Andrzej Dziech; Andrzej Czyżewski | |
| 09:50-10:20 | Keynote | Current Video Coding Standards: H.264/AVC, Dirac, AVS China, HEVC and VC-1 | Kamissety R. Rao |
| 10:20-11:00 | Session 1: Security Management Chair: M. Leszczuk |
Risk Assessment for SWOP Tele-Monitoring System Based on Fuzzy Cognitive Maps | Piotr Szwed; Pawel Skrzyński; Pawel Grodniewicz |
| INDECT Security Architecture | Manuel Urueña; Petr Machník; Marcin Niemiec; Nikolai Stoianov | ||
| 11:00-11:20 | Coffee Break | ||
| 11:20-13:20 | Session 2: Video Analysis incl. Intelligent Monitoringi Chair: Z. Wróbel |
People Detection and Tracking from a Top-View Position using a Time-of-Flight Camera | Carsten Stahlschmidt; Alexandros Gavriilidis; Joerg Velten; Anton Kummert |
| Video Analytics-Based Algorithm for Monitoring Egress from Buildings | Maciej Szczodrak; Andrzej Czyzewski | ||
| Visual Detection of People Movement Rules Violation in Crowded Indoor Scenes | Piotr Dalka; Piotr Bratoszewski | ||
| Survey of Recent Developments in Quality Assessment for Target Recognition Video | oel Dumke; Mikolaj I. Leszczuk | ||
| Depth Estimation in Image Sequences in Single-Camera Video Surveillance Systems | Aleksander Lamża; Zygmunt Wróbel; Andrzej Dziech | ||
| Detection of moving objects in images combined from video and thermal cameras | Grzegorz Szwoch; Maciej Szczodrak | ||
| 13:20-14:50 | Lunch Break | ||
| 14:50-15:50 | Session 3: Audio Analysis/Processing Chair: A. Czyżewski |
Comparison of different feature types for acoustic event detection system | Eva Vozarikova-Kiktova; Martin Lojka; Matus Pleva; Jozef Juhár; Anton Cizmar |
| Changing the voice of a subscriber on the example of an implementation of the PSOLA algorithm for the iOS and Android mobile platforms | Zbigniew Piotrowski; Michał Ciołek | ||
| Audio-visual surveillance system for application in bank operating room | Jozef Kotus; Kuba Łopatka; Andrzej Czyzewski; Georgis Bogdanis | ||
| 15:50-16:40 | Coffee Break/Expo | ||
| 16:40-18:00 | Session 4: Spatial Data Analysis Chair: A. Ligęza |
Mobile context-based framework for monitoring threats in urban environment | Szymon Bobek; Grzegorz Nalepa; Weronika Adrian |
| Anchor-free Localization Algorithm with Low- Complexity Method for Node Distance Estimation Enhancement Using ToA | Vladimír Cipov; Lubomir Dobos; Ján Papaj | ||
| Dynamic Map Architecture Evaluation Tools for ATAM | Piotr Szwed; Igor Wojnicki; Sebastian Ernst; Andrzej Glowacz | ||
| Rule-Based Knowledge Management in Social Threat Monitor | Mateusz Baran; Antoni Robert Ligęza | ||
| 18:00-20:00 | Break | ||
| from 20:00 | Dinner | ||
| Friday, 2013-06-07 | |||
| 10:00-11:30 | Session 5: Ethical Issues Chair: J. Derkacz |
Dilemmas of privacy protection in researches on public security. Data Protection Authority’s point of view | Piotr Drobek |
| We can protect our privacy online. NOT. | Piotr Konieczny | ||
| 11:30-11:50 | Coffee Break | ||
| 11:50-13:30 | Session 6: Network Data Analysis Chair: G. Dobrowolski |
Use of the bio-inspired algorithms to find global minimum in force directed layout algorithms | Jan Plucar; Patrik Dubec; Lukáš Rapant |
| Using sub-sequence patterns for detecting organ trafficking websites | Suraj Pandey | ||
| Two Methods for Detecting Malware | Maciej Korczyński; Gilles Berger-Sabbatel; Andrzej Duda | ||
| Downloading and analyzing images from the Internet in order to detect special objects | Mikolaj I. Leszczuk; Tomasz Piwowarczyk; Michał Grega | ||
| Multi-agent System for Pattern Searching in Billing Data | Łukasz Bęben; Bartlomiej Sniezynski | ||
| 13:30-15:00 | Lunch Break | ||
| 15:00-16:20 | iSession 7: Image/Video Processing Chair: K. R. Rao |
Practical Implementation of Visual Hash Functions for CCTV Footage Authentication | Katarzyna Żarnowiec; Pawel Korus; Andrzej Dziech; Andrzej Glowacz |
| 3D video compression using depth map propagation | Sergey Matyunin; Dmitriy Vatolin | ||
| Selective Robust Image Encryption For Social Networks | A. Emir Dirik; Nasir Memon | ||
| New robust video watermarking techniques based on DWT Transform and spread spectrum of basis images of 2D Hadamard Transform | Jakob Wassermann | ||
| 16:20-16:40 | Coffee Break | ||
| 16:40-17:40 | Session 8: Image Analysis Chair: J. Wassermann |
Knife Detection Scheme Based on Possibility Shell Clustering | Aleksandra Maksimova |
| Neural Network Regression of Eyes Location in Face Images | Krzysztof Rusek; Piotr Guzik | ||
| Feature Recycling Cascaded SVM Classifier Based on Feature Selection of HoGs for Pedestrian Detection | Alexandros Gavriilidis; Carsten Stahlschmidt; Joerg Velten; Anton Kummert | ||
| 17:40-18:00 | Best Paper/Closing | Andrzej Dziech; Andrzej Czyżewski | |
General Chair
- Andrzej Dziech, AGH University of Science and Technology, Poland
dziech (at) kt (.) agh (.) edu (.) pl
Committee Chairs
- Andrzej Dziech, AGH University of Science and Technology, Poland
dziech (at) kt (.) agh (.) edu (.) pl - Andrzej Czyżewski, Gdansk University of Technology, Poland
indect (at) sound (.) eti (.) pg (.) gda (.) pl
Technical Program Committee
- Atta Badii, University of Reading, United Kingdom
- Remigiusz Baran, Kielce University of Technology, Poland
- Alexander Bekiarski, technical University - Sofia, Bulgaria
- Fernando Boavida, University of Coimbra, Portugal
- Eduardo Cerqueira, Federal University of Para, Brazil
- Ryszard Choras, University of Technology and Life Sciences, Poland
- Michele Colajanni, University of Modena and Reggio Emilia, Italy
- Marilia Curado, University of Coimbra, Portugal
- Andrzej Czyzewski, Gdansk University of Technology, Poland
- Adam Dąbrowski, Poznan University of Technology, Poland
- Anne Demoisy, Skynet Belgacom, Belgium
- Marek Domański, Poznan University of Technology, Poland
- Andrzej Duda, Grenoble Institute of Technology, France
- Andrzej Dziech, AGH University of Science and Technology, Poland
- Andrzej Głowacz, AGH University of Science and Technology, Poland
- Michał Grega, AGH University of Science and Technology, Poland
- Nils Johanning, InnoTec Data, Poland
- Jozef Juhár, Technical University of Kosice, Slovakia
- Eva Kiktova, Technical University of Kosice, Slovakia
- Georgios Kioumourtzis, Ministry of Citizen Protection, Greece
- Marek Kisiel-Dorohinicki, AGH University of Science and Technology, Poland
- Christian Kollmitzer, FHTW Wien, Austria
- Bozena Kostek, Gdansk University of Technology, Poland
- Zbigniew Kotulski, Warsaw University of Technology, Poland
- Anton Kummert, University of Wuppertal, Germany
- David Larrabeiti, Universidad Carlos III de Madrid, Spain
- Mikołaj Leszczuk, AGH University of Science and Technology, Poland
- Antoni Ligęza, AGH University of Science and Technology, Poland
- Józef Lubacz, Warsaw University of Technology, Poland
- Tomasz Marciniak, Poznan University of Technology, Poland
- Wojciech Mazurczyk, Warsaw University of Technology, Poland
- Libor Michalek, VSB - Technical University of Ostrava, Czech Republic
- Suraj Pandey, University of York, United Kingdom
- George Papanikolaou, Aristotle University Of Thessaloniki, Greece
- Anna Paulson, NTIA/Institute for Telecommunication Sciences, USA
- Muttukrishnan Rajarajan, City University London, United Kingdom
- K. R. Rao, University of Texas at Arlington, USA
- Thomas Sablik, University of Wuppertal, Germany
- Haluk Sarlan, PSI Transcom GmbH, Germany
- Irena Stange, U. S. Department of Commerce, USA
- Nikolai Stoianov, Technical University of Sofia, Bulgaria
- Piotr Szczuko, Gdansk University of Technology, Poland
- Andrzej Szwabe, Poznan University of Technology, Poland
- Ryszard Tadeusiewicz, AGH University of Science and Technology, Poland
- Manuel Urueña, Universidad Carlos III de Madrid, Spain
- Guillaume Urvoy-Keller, Université de Nice Sophia-Antipolis, France
- Vladimir Vasinek, VSB – Technical University of Ostrava, Czech Republic
- Joerg Velten, University of Wuppertal, Germany
- Plamen Vichev, Technical University of Sofia, Bulgaria
- Eva Vozarikova Kiktova, Technical University of Kosice, Slovakia
- Zygmunt Wrobel, University of Silesia, Poland
- Jaroslav Zdralek, VSB – Technical University of Ostrava, Czech Republic
- Mariusz Ziolko, AGH University of Science and Technology, Poland
Organization Committee
- Jacek Dańda, AGH University of Science and Technology, Poland
- Jan Derkacz, AGH University of Science and Technology, Poland
- Sabina Drzewicka, AGH University of Science and Technology, Poland
- Andrzej Głowacz, AGH University of Science and Technology, Poland
- Michał Grega, AGH University of Science and Technology, Poland
- Piotr Guzik, AGH University of Science and Technology, Poland
- Paweł Korus, AGH University of Science and Technology, Poland
- Mikołaj Leszczuk, AGH University of Science and Technology, Poland
- Andrzej Matiolański, AGH University of Science and Technology, Poland
- Michał Pawłowski, AGH University of Science and Technology, Poland
- Małgorzata Janiszewska, AGH University of Science and Technology, Poland
- Krzysztof Rusek, AGH University of Science and Technology, Poland
Venue
The conference will take place in Krakow, one of the largest and oldest cities in Poland, the former the capital of Poland and a popular tourist destination. The venue will be at the Department of Telecommunications, AGH University of Science and Technology.
Address: ul. Czarnowiejska 78, 30-054 Krakow, Poland.
View Larger Map
Landmarks
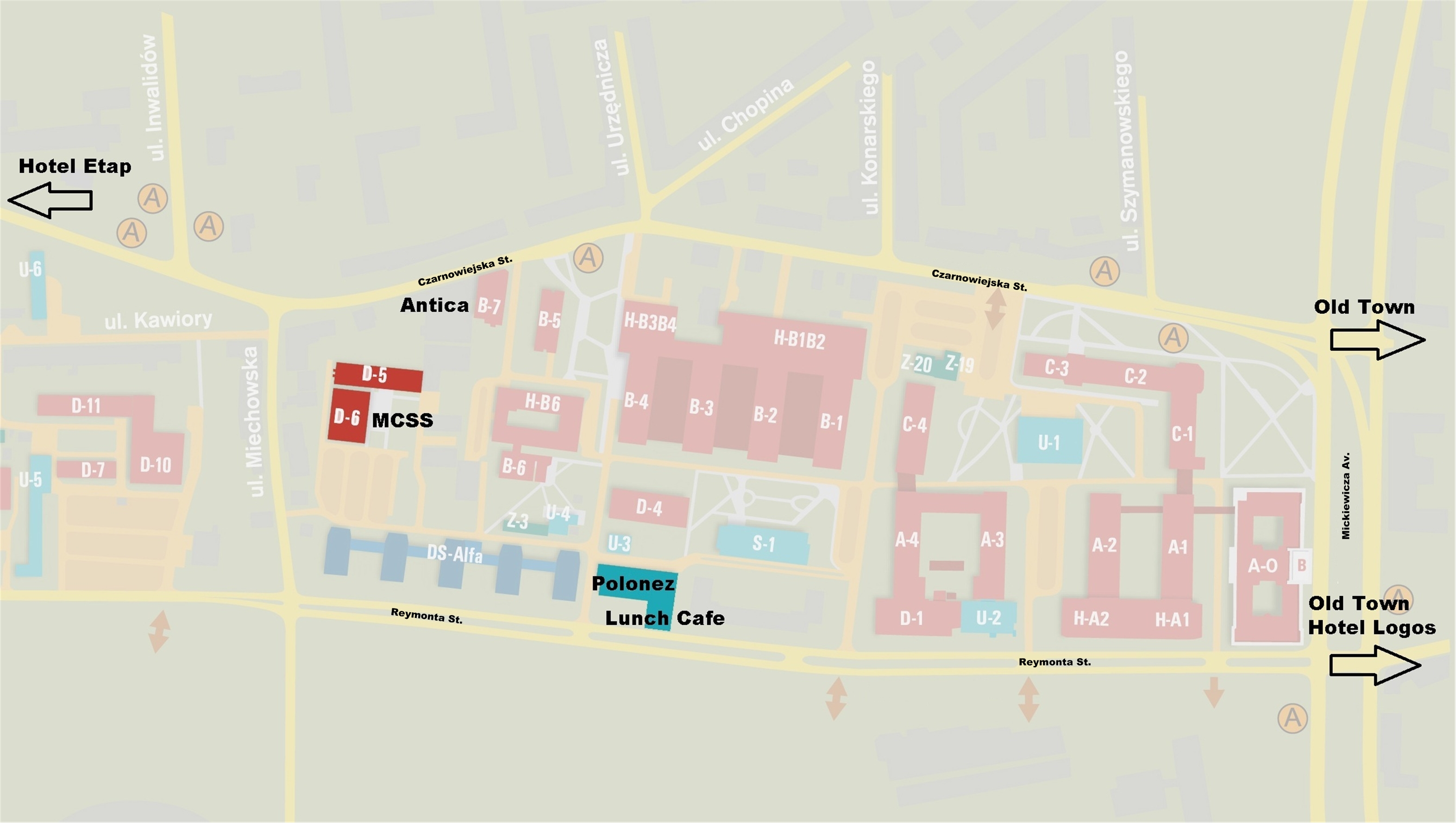
Conference Fees
The conference fee is € 350. This includes the proceedings, coffee breaks, lunches, and a conference dinner. Student registration (for undergraduate authors of accepted papers): 50% reduction of the regular fee (€ 175). IEEE member registration: 10% reduction of the regular fee (€ 315).Hotel Suggestions
Guest house Antica
ul .Czarnowiejska 7630-054 Kraków Voice: +48 12 631-23-50
Fax: +48 12 633-49-52
Email: antica@jordan.pl
Web: http://www.antica.jordan.pl
Hotel Leopolis ***
Ul. Juliusza Lea 253 A30-133 Kraków Voice: +48 012 636 51 95
Fax: +48 012 637 70 05
Email: leopolis@leopolis.com.pl
Web: http://www.leopolis.com.pl
Novotel Krakow City West
Ul. Armii Krajowej 1130-150 Krakow Voice: +48 12 622 64 92
Fax: +48 12 622 64 94
Email: H3407-RE1@accor.com
Web: http://www.novotel.com
Hotel Polonez
ul. Reymonta 1530-059 Kraków Voice: +48 (12) 292 82 94/95
Voice: +48 (12) 634-19-54
Fax: +48 (12) 631 87 31
Email: recepcja@hotel-polonez.pl
Web: http://www.hotel-polonez.pl/
Radisson Blue
ul. Straszewskiego 1731-101 Krakow Voice: +48 12 618 88 88
Email: magdalena.goc@radissonblu.com
Web: http://www.radissonblu.com
Ibis budget Kraków Bronowice
Al. Armii Krajowej 11a30-150 Kraków Voice: +48 (12) 626 11 45 / +48 505 198 336
Fax: +48 (12) 626 20 60
Email: H6605@accor.com
Web: http://www.ibisbudget.com





